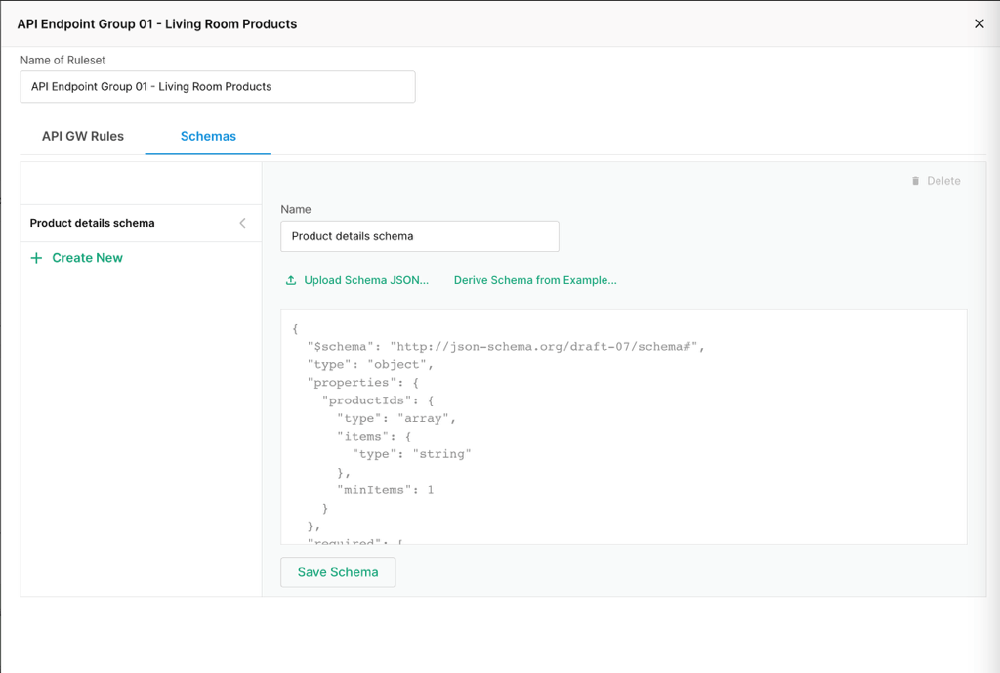
When I worked with Edgio, I architected, built, and maintained our API Security feature. Below is my overview of it, described solely using public resources, though you may review the current documentation yourself at the following links:
- https://docs.edgecast.io/applications/v7/security/api_security
- https://docs.edgecast.io/applications/v7/security/waf
- https://www.edgecast.io/post/mastering-api-security-from-discovery-to-defense
What is API Security?
API Security is a module of the CDN’s firewall which allows customers to configure what sort of requests are allowed, and to which endpoints. Specifically, the customer defined the following:
- a valid JSON schema (defined in RFC 8927)
- a web API endpoint of theirs
- request methods to validate (e.g. GET, POST, PUT, DELETE, etc.)
- A set of JSON Web Keys (JWKs, defined in RFC 7517)
JSON Schema example
{
"$id": "https://example.com/blog-post.schema.json",
"$schema": "https://json-schema.org/draft/2020-12/schema",
"description": "A representation of a blog post",
"type": "object",
"required": ["title", "content", "author"],
"properties": {
"title": {
"type": "string"
},
"content": {
"type": "string"
},
"publishedDate": {
"type": "string",
"format": "date-time"
},
"author": {
"$ref": "https://example.com/user-profile.schema.json"
},
"tags": {
"type": "array",
"items": {
"type": "string"
}
}
}
}
Valid Request Body
{
"title": "New Blog Post",
"content": "This is the content of the blog post...",
"publishedDate": "2023-08-25T15:00:00Z",
"author": {
"username": "authoruser",
"email": "author@example.com"
},
"tags": ["Technology", "Programming"]
}

Why?
- Companies have many APIs that may not fully be routinely inventoried or updated
- APIs are major attack vectors and are more connected to backend infrastructure
- The Principle of Least Privilege
The OWASP Foundation suggests three categories for maintaining API Security:
- API Security Posture: Creates an inventory of APIs, the methods exposed and classifies the data used by each method.
- API Runtime Security: provides protection to APIs during their normal running and handling of API requests.
- API Security Testing: Dynamic assessment of an API’s security state.
The API Security feature I built targeted categories (1) and (2) after being combined with our ML-powered API Discovery feature I helped build.
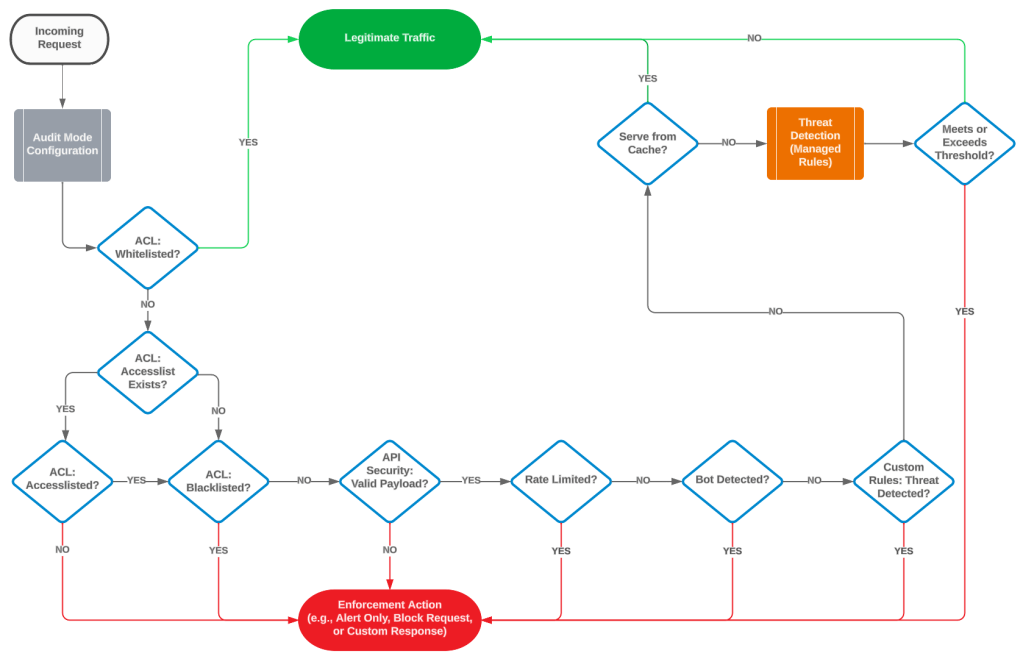
How it functions
As a mature, partially open-source, firewall operating at a massive scale, the validation process for requests was part of a larger customer-configurable decision-tree. This tree involved Access control lists, rate-limiting, (ML-powered) threat detection, etc. Below is a diagram showing the flow of a request: